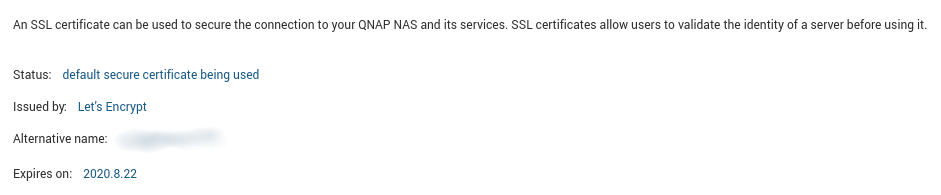
I’ve been trying to setting up DDNS for my QNAP NAS with SSL connection. I don’t want to use the QNAP Cloudlink DDNS service because I wanted to use QVPN service to globally gate all traffic going out from QNAP. And that disables the QNAP Cloudlink service from getting the real IP address for my NAS.
The basic logic goes along this tutorial: How to set up a free dynamic hostname with SSL cert using Google Domains, except the following moving parts:
-
I chose to use Cloudflare instead of Google Domains - if you point your domain registrar to Cloudflare’s name servers, you get access to Cloudflare’s REST API for managing DNS records programmatically: https://api.cloudflare.com/#dns-records-for-a-zone-update-dns-record
This would mean that you can setup free DDNS for virtually any domain registrar, just by using a different
curlcall in your DDNS cron script:#!/usr/bin/env bash # DDNS cron script IP=$( dig +short myip.opendns.com @resolver1.opendns.com ) CloudFlareZoneId="<your-zone-id>" CloudFlareRecordId="<your-dns-record-id>" CloudFlareApiKey="<your-api-key>" curl -X PUT \ "https://api.cloudflare.com/client/v4/zones/${CloudFlareZonId}/dns_records/${CloudFlareRecordId}" \ -H "X-Auth-Email: <your_cloudflare_registered_email>" \ -H "X-Auth-Key: ${CloudFlareApiKey}" \ -H "Content-Type: application/json" \ --data "{\"type\":\"A\",\"name\":\"lby\",\"content\":\"${IP}\",\"ttl\":60,\"proxied\":false}" -
I’m using DD-WRT router as the DDNS client and certificate renewer. This is because my QNAP NAS is behind the VPN and cannot get its real IP for updating the Cloudflare DNS record. However, this has brought some difficulties:
certbotis not available on EntWare - the solution is to usegetssl.- This DD-WRT router needs to
sshonto QNAP NAS to upload the generated certificates, and setting up ssh keys for a DD-WRT router is not very easy: need to installopenssh-clientand restart the router first to get away fromdropbearssh keys. getsslconfiguration: The Apache configuration for the QNAP NAS is not easily figured out, thus I don’t know how to correctly upload the generated certificates and keys to my QNAP NAS.
Below is my NAS setup:
- QNAP running QVPN client, all outgoing traffic behind VPN provider.
- DD-WRT router running EntWare, with cron script running as DDNS client.
getsslrunning as another cron job on the router, automatically renews certificates and upload them to QNAP NAS and restarts the web server on NAS.
The main issues I faced was to configure getssl to upload and run the correct
commands to update my QNAP NAS, and below are the key code snippets that made
QNAP use my DDNS certificates instead of its default QNAP certificates:
# per-domain getssl.cfg
# Need to create this directory on QNAP manually first, otherwise getssl will
# fail.
ACL=('ssh:admin@<qnap>:/home/httpd/.well-known/acme-challenge')
...
# Location for all your certs, these can either be on the server (full path name)
# or using ssh/sftp as for the ACL
DOMAIN_CERT_LOCATION="ssh:admin@<qnap>:/etc/stunnel/getssl.cert.def"
DOMAIN_KEY_LOCATION="ssh:admin@<qnap>:/etc/config/stunnel/getssl.key.def"
And below is the cron job that I’m setting up to run every day:
#!/usr/bin/env bash
# Let's Encrypt automatic renew cron script.
getssl <your-domain-here> && \
ssh admin@<qnap> \
'/etc/init.d/stunnel.sh generate_cert_key && /etc/init.d/stunnel.sh restart'
And now I see that QNAP’s “Security” administration page show the Let’s Encrypt certificate instead of QNAP’s default one: